This class provides the functionality of a secret (symmetric) key generator. Key generators are constructed using one of the getInstance class methods of this class. KeyGenerator objects are reusable, i.e., after a key has been generated, the same KeyGenerator object can be re-used to generate further keys.
- Aes 128 Random Key Generator Wheel
- Random Letter Generator
- Aes 128 Random Key Generator
- Aes 128 Random Key Generator Online
- Aes 128 Random Key Generator Java
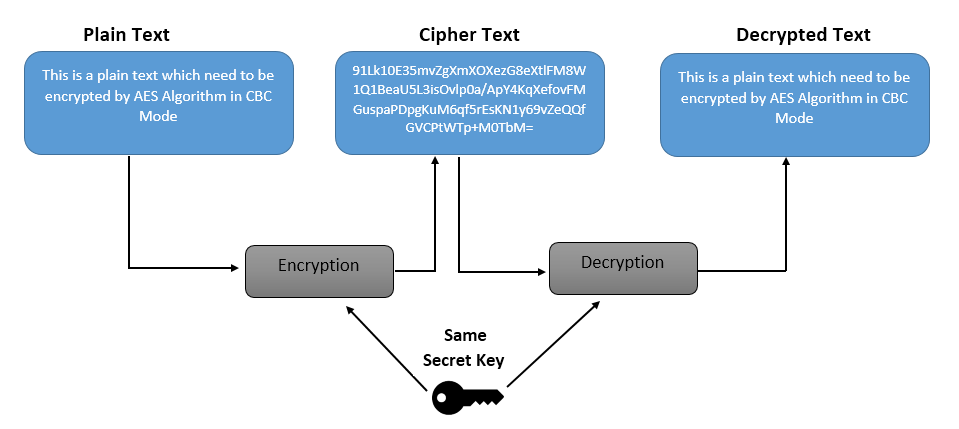
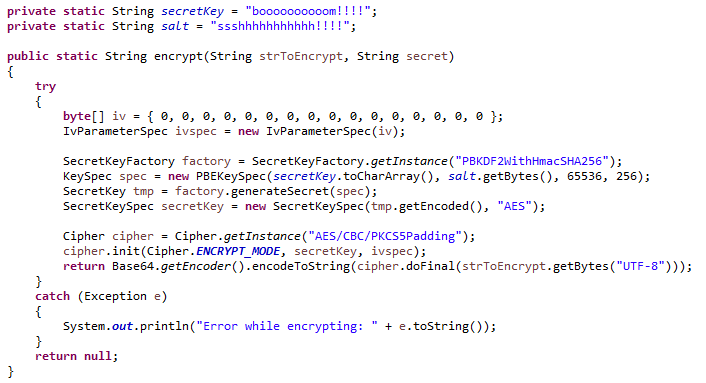
The AES algorithm is an iterative, symmetric-key block cipher that supports cryptographic keys (secret keys) of 128, 192, and 256 bits to encrypt and decrypt data in blocks of 128 bits. The below figure shows the high-level AES algorithm: If the data to be encrypted does not meet the block size of 128 bits requirement, it must be padded. Generating an AES key An AES key is a random bitstring of the right length. For a 128-bit AES key you need 16 bytes. For a 256-bit AES key you need 32 bytes.
Symmetric key cryptography definition
Symmetric key cryptography that sometimes called symmetric encryption, is an encryption type in which a single key is used both to encrypt and decrypt messages.
Its concept is not new, as an early example of its usage is contributed to the Roman General Julius Caesar that is known as Caesar Cipher.
It is a relatively easy way of encryption a text or data, in which only the sender and receiver of a message can read it by using a single shared key.
This process of encryption is relatively fast. It’s easy to use, which makes it a great option for various types of data transfers.
From secure online banking to ordering goods from online shops, almost any process that deals with data transfer use a form of symmetric key cryptography.
In the following article, we will explain how it works, what are its usages, types, and advantages.
What is exactly symmetric key cryptography?
In its simplest form, Symmetric key cryptography is a type of encryption that uses the same shared key to encrypt and decrypt data.
This type of encryption algorithm converts data to a form that could not be understood by anyone who does not possess the secret key to decrypt it.
Then, the receiver uses the secret key, the algorithm reverses the process and decrypt data to its original understandable form.
This key that is used by both sender and receiver can be a specific password or can be random letters or numbers that are generated by a secure random number generator (RNG).
To understand it clearer, let break symmetric key cryptography to its main steps:
– The sender has a secret message that no one except the receiver could read it. So they use an encryption key to encrypt their massage
– The encrypted message that is called ciphertext turns to scrambled random letters that could not be read by anyone without knowing the secret key
– Recipient uses the original shared decryption key to transform the ciphertext back into a readable message
Because this process works only by a single key to encrypt/decrypt a message, it is called symmetric.
Many people think it is used in the cryptocurrency world to encrypt transactions, which is a false belief.
Bitcoin and other cryptocurrencies typically use asymmetric cryptography that provides two keys (public key and private key) to decrypt data.
We explain the difference between these two types of encryption in more detail in the following.
Symmetric key cryptography history
While its usage in encoding digital data in computers is relatively new and comes back to the mid-1900s, the concept is not new at all.
As we mentioned earlier, symmetric cryptography is thought to have been created thousands of years ago.
Other examples of its historical usages date back to the 1500s when Videnere Cipher was invented.
Aes 128 Random Key Generator Wheel
However, in modern days several types of Symmetric key cryptographies are developed to be used by computers and digital devices to securely transfer data.
Some of these types will be explained in the following. But first, let take a look at its very first example, Caesar Cipher.
How does Caesar Cipher work?
This easy method of the encryption process is a good example to understand the basics of cryptography. It is also known as substitution or shift cipher.
This method is thought to be used by Ceasar to communicate with army generals without anyone being able to read the message even if its carriers were intercepted.
It uses a cipher that also could be known as an algorithm that defines some steps that should be used to convert plain text into unreadable ciphertext.
Random Letter Generator
This method simply applies a rule to shift readable letters of a message to an unreadable message that could be decrypted using its rule.
Symmetric key cryptography algorithms types
The example above is a very basic and primary form of symmetric encryption, as several types of more complicated algorithms are developed to use in the modern era.
However, in modern cryptography, two main types of symmetric encryptions are available:
– Block algorithms use a specific secret key to encrypt set lengths of bits in blocks of electronic data.
While the data is being encrypted, the system keeps data in memory waiting for complete blocks
– Stream algorithms: data is encrypted as it is streamed instead of being kept in the system’s memory.
Stream algorithm, also called stream cipher, is somehow faster, requires lower computing, and however, decryption could be easier than block algorithm, which is also known as a block cipher.
However, as we mentioned earlier, these two main types are the general categories of symmetric-key cryptography, and each of these categories contains several algorithms.
Some well-known examples of symmetric encryption algorithms include:
– AES (Advanced Encryption Standard)
– DES (Data Encryption Standard)
– IDEA (International Data Encryption Algorithm)
– Blowfish (Drop-in replacement for DES or IDEA)
– RC4 (Rivest Cipher 4)
– RC5 (Rivest Cipher 5)
– RC6 (Rivest Cipher 6)
Among all these algorithms, RC4 is a stream cipher, while all others are block ciphers.
DES and AES could be considered as the most important types of symmetric key cryptography methods, which are explained more in the following.
Data Encryption Standard (DES)
DES was the first standardized cipher for securing electronic communications in modern computing.
It was used in two variations: 2-key or 2DES, and 3-key or 3DES. With the increase of processing power of modern computers, the original DES is not used anymore as it is considered weak.
However, its 3-key variation, 3DES is still used in EMV chip cards.
Advanced Encryption Standard (AES)
AES is the most commonly used symmetric encryption algorithm that is a standard set by the U.S. National Institute of Standards and Technology in 2001 for encryption of electronic data.
AES supersedes DES that had been in use from 1977. According to the National Institute of Standards and Technology, AES cipher has a block size of 128-bits, but it can also have three different key lengths:
– AES-128
– AES-192
– AES-256
However, a 128-bit key would take billions of years to guess using common computer hardware. The longer the encryption key, the harder becomes to decrypt it.
Symmetric key cryptography use cases
As we mentioned earlier, this type of encryption is an old method that is substituted by several alternative methods such as asymmetric key cryptography.
However, old symmetric encryption provides a faster and more efficient way to encrypt data, which makes it more suitable for encrypting large amounts of data, for example in database encryption.
In these cases, the secret key should only be available to the database itself to encrypt and decrypt.
However, symmetric-key cryptography is used in the following activities:
– Payment applications and banking products, such as card transactions
– Validations and confirmations where the sender of a message should be identified
– Random number generation (RNG) or hashing algorithms
– Data At Rest
– HTTPS and website security
Symmetric key cryptography in Banking
As you might know, several rules are deployed in banking standards to make sure the users’ information and accounts are safe.
The Payment Card Industry Data Security Standards (PCI DSS) is a series of 12 requirements that organizations and businesses that accept credit cards must adopt.
Symmetric key cryptography is directly included in these rules, and it is used to protect at-rest cardholder data.
Aes 128 Random Key Generator
It should be noted that in many cases symmetric encryption is used along with asymmetric encryption to provide required encryption and cryptography.
The PCI DSS also requires businesses to implement asymmetric encryption to provide security of in-transit data.
Factors contributing to symmetric key cryptography security
Remember our encrypted message “Hey baby”, and imagine someone tries to decrypt it without knowing its rule.
In this case, their guesses could be extended to all potential spaces between alphabet letters and In other words, it takes at least 26 various guesses for every letter to figure out the true message if the main principle that the letters are replaced by the following letters could be known.
In the real world, the strength of a cryptographic key depends on a series of specific factors:
– The length of the key
– The randomness of how the key is generated
– How long it takes to decode individual components
In other words, someone who might attempt to decode a symmetric key can use certain algorithms to begin the process of guessing the true key, but its success could take such a long time that make it not practical.
Symmetric key cryptography and asymmetric encryption
Two major methods of encrypting data in modern computer systems include symmetric encryption and asymmetric encryption methods.
The main difference between these two methods is that in asymmetric systems two keys are used rather than the one used by symmetric encryption.
As you know, Bitcoin and other cryptocurrencies provide two keys:
– Public key
– Private key
These two key correspond to each other, and the private key should be used to generate the public key, which in its turn, can not be used to determine the private key.
Aes 128 Random Key Generator Online
However, asymmetric encryption outputs are very harder to guess or decode but are significantly slower than symmetric encryptions.
The mathematical calculations used in generating asymmetric encryption are very complicated, and their explanation requires another article.
Closing Thoughts
Symmetric key cryptography is a relatively simple way to encode or encrypt data in a form that could be decoded or decrypted with a single shared key.
This procedure, in its basic and primary form, was used thousands of years ago.
Since it is a relatively easy method and works faster than asymmetric encryption methods, in many cases it provides more efficiency.
Aes 128 Random Key Generator Java
In other cases, where the fast transfer of secure data is required, symmetric encryption could be considered as a better option, and that’s why typically it is used along with asymmetric encryption in banking systems.